privacyIDEA 2.18 is out!
privacyIDEA Authentication System
 privacyIDEA is an authentication system. Quite a while ago we started to drop the sole OTP statement. privacyIDEA is managing authentication objects. Yes, a classical OTP key fob token is an object a user can use to authenticate. As is a smartphone.
privacyIDEA is an authentication system. Quite a while ago we started to drop the sole OTP statement. privacyIDEA is managing authentication objects. Yes, a classical OTP key fob token is an object a user can use to authenticate. As is a smartphone.
But privacyIDEA already facilitated SSH keys. These files are objects, a user can use to authenticate.
Trust the privacyIDEA Certificate Authority
In this release 2.18 we improved the functionalities of the local CA. privacyIDEA provides an interface to connect to certificate authorities to ask them to issue certificates for the users.
Connectors can plug into this interface. At the moment we are providing a “local CA” connector, which connects to a locally running OpenSSL based CA. With privacyIDEA 2.18 setting up such a local CA is much easier. The local CA also supports automatically generating the CRL, if a certificate token is revoked. The CA now also can handle certificate templates with different X.509 extensions and different validity periods.
For a complete list of all features, enhancements and fixes see the Changlog at Github.
Use a local CA
Certificates are a special token type with privacyIDEA. The documentation at readthedocs has more detailed information about the certificate handling in privacyIDEA. We will give you a quick idea what is new in regards to the local CA.
Create your local CA
You can use the pi-manage tool to create a CA Connector, list all CA Connectors and also create CRLs.
pi-manage ca create myCA
This will create a CA Connector of type “local CA”. You are asked the following questions:
Creating CA connector of type local. In which directory do you want to create the CA [./ca]: /etc/privacyidea/myCA What should be the keysize of the CA (2048/4096/8192) [4096]: How many days should the CA be valid [1800]: 7200 What is the DN of the CA [/CN=myCA]: How many days should the CRL be valid [30]: 60 What should be the overlap period of the CRL in days [5]: 10 ============================================================ Directory : /etc/privacyidea/myCA CA DN : /CN=myCA CA Keysize : 4096 CA Validity: 7200 Validity of issued certificates: 365 CRL validity: 60 CRL overlap : 10 Is this configuration correct? [y/n]
When answering “yes”, the CA will be created on the file system and also within privacyIDEA the CA Connector definition, that links to this CA will be created.
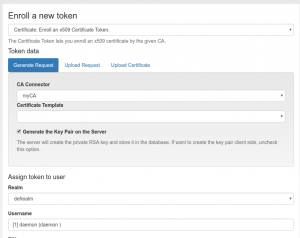
Enroll Certificate
Now, the administrator can immediately start enrolling certificates for the users. The certificates will be issued by “myCA”, which we just created.
At the moment, we can not use certificate templates, we need to create an additional configuration file to do so.
A templates.yaml defines, which special X.509 extensions from the openssl.cnf file should be used and what should be the number of days, this very certificate will be issued for.
A file /etc/privacyidea/myCA/templates.yaml might look like this:
user: days: 365 extensions: "user" email: days: 750 extensions: "email"
This file needs to be specified at Config -> CAs -> myCA.
This way you can enroll certificates with different attributes for certain purposes.
Installation and servies
There are different ways to install privacyIDEA which are well documented in the online documentation. Checkout the Github repository to file and issues, post your ideas or pull requests. Or simply star the project.
If you are running privacyIDEA mission critical you might want to take a look at the privacyIDEA Enterprise Edition provided by NetKnights GmbH.