Gaining higher security with smartcards and Four-Eyes-Tokens

Today we put privacyIDEA 3.5 under your Christmas tree. Unwrap it and you will find a lot of enhancements. One of the most important features is that version 3.5 does the first step to also support smartcard management. For high security environments we drastically imrpoved the workflow of Four-Eyes-Tokens.
Let’s do this togeather – Four-Eyes-Tokens
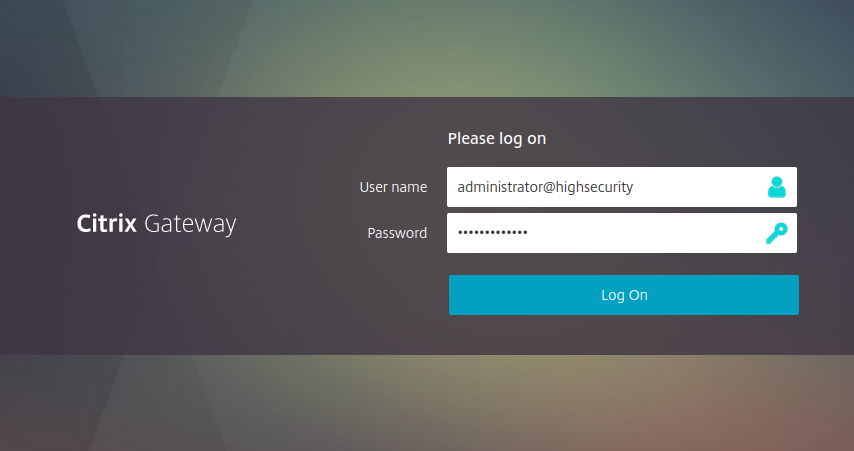
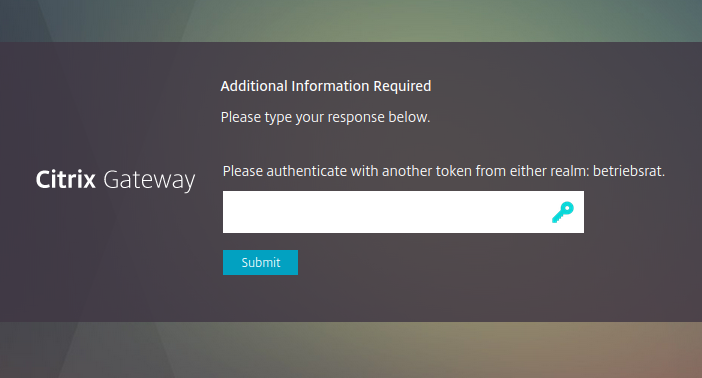
Using the Four-Eyes-Tokens the administrator can define how many users from several different groups should come togeather when the account – the holder of the Four-Eyes-Token – wants to authenticate. This way you can define, that this account worthy of protection can only be used if e.g. two IT administrators and one member of the works council come togeather and use their own 2nd factors to authenticate.
The Four-Eyes-Token has been around for a while in privacyIDEA. But now we are using the Multi–Challenge, that was introduced in privacyIDEA 3.4, to heavily improve the workflow and authentication flow. It is totally transparent to our application plugins and the RADIUS protocol, so that it can be used e.g. with Citrix Netscaler.
So in the first step the first person uses his credentials and 2nd factor. Then in a 2nd step the second user is asked for his credentials and 2nd factor.
Do not copy, rather sign! – PIV smartcards with privacyIDEA
Smartcards are interesting devices, that have certain disadvantages in handling but also come with advantages and features, that allow for completely other use cases like offline authentication, decryption or document signing.
privacyIDEA was already capable of enrolling and manageing x509v3 user certificates. As a first step to better support smartcards, privacyIDEA 3.5 now can require that certificate requests are generated on a PIV smartcard. This is done by
using policies to force the presence of an attestation certificate during enrollment. The attestation certificate confirms, that actually the key pair was generated on a smartcard and there is no copy of the private key.
This was successfully done with the Yubikey 5 and a corresponding enrollment tool. We will continue working on imrpoving the privacyIDEAs smartcard capabilities.
Make the admin’s life easier – serveral enhancements
Tokens
The Push token gets a lot of feedback in the community. So we are continuously improving it. User certain conditions a smartphone device can renew its firebase token, that is used to communicate with Google’s firebase push service. The smartphone app can now contact the privacyIDEA server to update this firebase token.
The registration token is a long “registration code”, that can be used to authenticate once during enrollment processes. The admin can now configure a policy to define the length and contents of the registration code.
A Webauthn token should also provide a signature counter, that is used to identify and avoid cloned tokens. However, not all cheap devices implement this. privacyIDEA now also allows to use Webauthn tokens without a signature counter on demand.
Hardware tokens come with a seed file. privacyIDEA can import a lot of different formats, also PSKC which is defined in RFC6030. The import of PSKC files now also verifies the MAC of the token secrets.
The questionnaire token can now ask more than one question during the authentication process.
Event handlers and policies
The policies may now contain additional extened conditions from the tokeninfo attributes. This can be any arbitrary attribute, so that the admin could define policies, that e.g. allow the authentication at certain applications with a hardware token but not with a software token.
The Tokenhandler can choose the SMS Gateway Identifier or the SMTP Identifier when enrolling an SMS or respectively an Email token.
The Tokenhandler can now increase and decrease the fail counter and also set the Maxfail counter.
The Web UI
Several enhancements allow a smoother work experience for administrators and service desk users. The admin can define a policy to hide certain columns in the audit log. This way the service desk users only see this information, which they really need. Also, the audit log contains the start time, the end time and the duration of a request. This way it is easy to filter or search for long running requests to debug authentication problems. In the dashboard the usernames of the users with failed authentications are displayed with a short link to their user details. This helps the service desk to immidiately find failing users and offer quickers support.
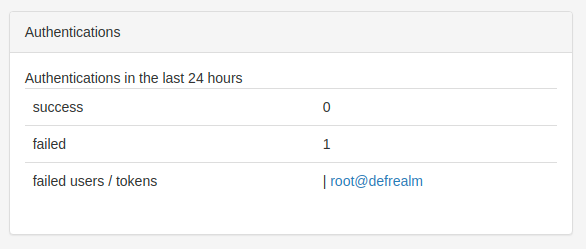
The WebUI now supports the PIN change via multi-challenge response.
The conditions for event handlers and actions for policies have been redesigned to make them look the same and easily searchable.
Managing privacyIDEA
In certain setups you might have a testing environment, a staging environment and a production environment. Configuration changes are often first tested in the testing environment and then transferred to the staging and production environment.
The pi-manage script has a new sub command to export and import resolver configuration, that will help in such scenarios.
The full list of features, enhancements and fixes can be found in the Changelog.
Get privacyIDEA
privacyIDEA is an enterprise grade, extremely flexible multi-factor authentication system, that can adapt to your needs and that lets you automate a lot of tasks. Using privacyIDEA will increase your security. Migrating from other mult-factor
systems to privacyIDEA will ease your life. People have done this and dropped many well-known, but old and crusty authentication systems. Take a look at privacyIDEA and join the community.
It is freely available via the Python package index and via community repositories for Ubuntu LTS 16.04, 18.04 and 20.04.
The company NetKnights provides an Enterprise Edition with Service Level Agreements and stable packages for Ubuntu LTS and Red Hat Enterprise Linux/CentOS.
If you want to stay tuned, join the community forum or subscribe the NetKnights’ newsletter.




Start the discussion at community.privacyidea.org